|
Level: 1
ADR Info
Additional Info
|
The purpose of this guide ? is to introduce you to the art of bytecode hacking, also known as looking for array of bytes (AoBs). Now, if you are already a proficient bytecode hacker, these guides will probably do very little to help you, as most of my knowledge comes from this forum. However, my knowledge has accumulated over months of looking through various tips here and there in different threads, and I wished to compile it all into one place. So, this thread is the start of a series of guides that will hopefully inspire many more bytecode hackers. Myself, I started with limited experience in C++ and absolutely no knowledge of ActionScript, the language used in Flash. I would suggest learning the basics of coding, perhaps through an online tutorial. Coding in any programming language helps immensely, but is not necessary to learning how to bytecode hack. You just need to be able to adapt quickly and be very patient. I first learned about bytecode hacking through this guide. This is pretty basic and the tools in this video guide are, for the most part, outdated. However, there are some extremely helpful discussions in this thread (if you care to look through ~19 pages of posts). One of the most amazing hacks is shown in Ignored's tutorial on the Farmville game here. A great tutorial by deity on how to find functions through sprites and changing them accordingly here. Now, let's begin by becoming acquainted with the tools and how bytecode hacking works. Step 1: Download the .swf file In Firefox, the most common way is through AdBlock Plus, in which you simply look for the .swf file that has loaded on the page. More details here. In Google Chrome, one can use a slightly different method as outlined here. Kongregate: This will work for most kongregate games, and it is usually in the form of Code: http://chat.kongregate.com/gamez/####/####/live/GAME_NAME.swf?kongregate_game_version=########### For example, for Robot Wants Kitty, the file is Code: http://chat.kongregate.com/gamez/0007/3913/live/robotkitty_kong.swf?kongregate_game_version=1268274573 Newgrounds: This will work for most Newgrounds games, and is usually in the form of Code: http://uploads.ungrounded.net/#####/#####_GAME_NAME.swf For example, the game Hippolyta is at Code: http://uploads.ungrounded.net/530000/530069_Amazon.swf Note: Sometimes, due to encryption or something, you will not be able to find the correct file, or perhaps the file is unreadable. This can often be circumvented using Mr.White's great tool called swfmdump, which dumps the file from the computer memory. Step 2: Decompile the .swf file The tool that is used by the members on this forum (and is highly recommended) is called SoThink. You can easily get a torrent for SoThink and its key (newest version is ~5.4). Now, open the .swf file with the installed decompiler. With SoThink, you can right-click on the file and click on SoThink, or alternatively, you can open the file through Sothink itself. Navigating SoThink shouldn't be too difficult. After you open it, hopefully it should look something like this:  Expand on the right side (circled in red) and you should see the different components. Usually, all the code is under "Action" so let's see what's there. Let's look with the section that says "Game."  If you look on the top (circled in red), there's 3 different types of views for the same piece of code. Source Code is the human-readable code, or what it looks like before decompiling. P-Code is the computer instructions associated with this code. 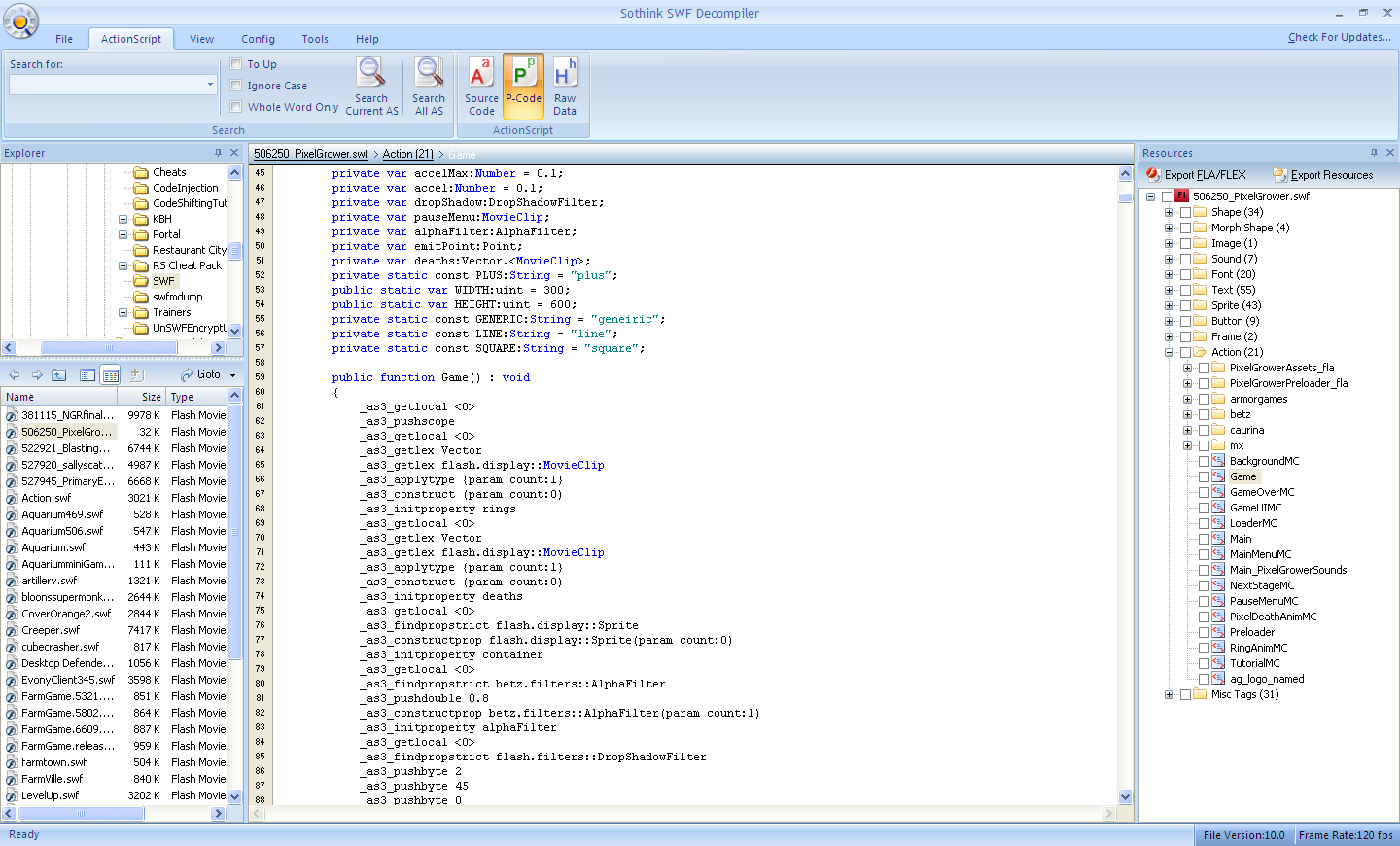 Raw data is all the bytes that are fed to the computer. These bytes are stored in the computer's memory, and it is these bytes that we want to change. Step 3: Changing the bytecode This is the most difficult part to become proficient at, and knowing what to change and what to change the bytes to requires a lot of skill; it is what makes the greatest hackers on this forum so great. Any experience in coding really helps, but is not necessary at all. Now, with AS2 (used in Flash 8 or before), you can use a tool called Flasm. Details are given in this video guide. However, most games these days are coded with AS3 (Flash 9 or later), so Flasm is useless. Let's first see the basics of how bytecode works. Take the game Creeper World Training Sim. After decompiling and searching through it, I find a function called calculateDamage.  You can see at the top it defines several variables (that don't really matter to us), and then it goes right into calculating the damage and executing commands based on the damage. The bytecode that corresponds to this code is here: Code: private function calculateDamage() : Boolean { //d0 _as3_getlocal <0> //30 _as3_pushscope //28 _as3_pushnan //d5 _as3_setlocal <1> //24 00 _as3_pushbyte 0 //63 04 _as3_setlocal <4> //27 _as3_pushfalse //d6 _as3_setlocal <2> //24 ff _as3_pushbyte -1 //d7 _as3_setlocal <3> //10 6c 00 00 _as3_jump offset: 108 //09 _as3_label //24 ff _as3_pushbyte -1 //63 04 _as3_setlocal <4> //10 59 00 00 _as3_jump offset: 89 //09 _as3_label //60 1b _as3_getlex com.wbwar.creeper::GameSpace //66 f9 0d _as3_getproperty instance //66 b6 01 _as3_getproperty glop //66 99 06 _as3_getproperty data //60 8a 03 _as3_getlex gameSpaceX //62 04 _as3_getlocal <4> //a0 _as3_add //60 8b 03 _as3_getlex gameSpaceY //d3 _as3_getlocal <3> //a0 _as3_add //60 1b _as3_getlex com.wbwar.creeper::GameSpace //66 97 09 _as3_getproperty WIDTH //a2 _as3_multiply //a0 _as3_add //66 e5 12 _as3_getproperty {} //75 _as3_convert_d //d5 _as3_setlocal <1> //d1 _as3_getlocal <1> //60 b7 01 _as3_getlex com.wbwar.creeper::Glop //66 c4 0f _as3_getproperty MIN_HEAT //0f 29 00 00 _as3_ifnge offset: 41 //26 _as3_pushtrue //d6 _as3_setlocal <2> //5e f9 02 _as3_findproperty health //60 f9 02 _as3_getlex health //60 bf 03 _as3_getlex com.wbwar.creeper:Weapon::damageAmt //a1 _as3_subtract //68 f9 02 _as3_initproperty health //60 f9 02 _as3_getlex health //24 00 _as3_pushbyte 0 //0c 11 00 00 _as3_ifnlt offset: 17 //5e f9 02 _as3_findproperty health //24 00 _as3_pushbyte 0 //68 f9 02 _as3_initproperty health //5d a4 03 _as3_findpropstrict destroy //4f a4 03 00 _as3_callpropvoid destroy(param count:0) //26 _as3_pushtrue //48 _as3_returnvalue //c2 04 _as3_inclocal_i <4> //62 04 _as3_getlocal <4> //24 01 _as3_pushbyte 1 //16 9f ff ff _as3_ifle offset: -97 //c2 03 _as3_inclocal_i <3> //d3 _as3_getlocal <3> //24 01 _as3_pushbyte 1 //16 8d ff ff _as3_ifle offset: -115 //d2 _as3_getlocal <2> //96 _as3_not //2a _as3_dup //12 05 00 00 _as3_iffalse offset: 5 //29 _as3_pop //60 8d 03 _as3_getlex building //96 _as3_not //12 1f 00 00 _as3_iffalse offset: 31 //5e f9 02 _as3_findproperty health //60 f9 02 _as3_getlex health //2f 15 _as3_pushdouble 0.01 //a0 _as3_add //68 f9 02 _as3_initproperty health //60 f9 02 _as3_getlex health //60 99 03 _as3_getlex maxHealth //0e 09 00 00 _as3_ifngt offset: 9 //5e f9 02 _as3_findproperty health //60 99 03 _as3_getlex maxHealth //68 f9 02 _as3_initproperty health //d2 _as3_getlocal <2> //48 _as3_returnvalue } // end function Now we must decide which bytes corresponds to which code. For now, we'll use key words such as "Destroy" or "health". So, Code: health = 0; destroy(); return true; corresponds to something like this: Code: //5e f9 02 _as3_findproperty health //24 00 _as3_pushbyte 0 //68 f9 02 _as3_initproperty health //5d a4 03 _as3_findpropstrict destroy //4f a4 03 00 _as3_callpropvoid destroy(param count:0) //26 _as3_pushtrue //48 _as3_returnvalue Note that in structuring bytes, it first lists the variable such as health, and then it pushes the byte 0 to assign 0 to health. In later tutorials, I will go into more detail on pushing numbers and such. Anyways, this piece of code corresponds to a structure that the player builds. Obviously, we don't want our own structures destroyed, so we'll NOP out the call to the function "destroy." So, copy+paste the 2 lines of code that correspond to this line: Code: destroy(); which would be Code: //5d a4 03 _as3_findpropstrict destroy //4f a4 03 00 _as3_callpropvoid destroy(param count:0) The AoB we search for would be 5d a4 03 4f a4 03 00 and to NOP it out, we replace it with 02: 02 02 02 02 02 02 02 And there you have it! We have now found an AoB for invincible units! Step 4: Using the bytecode hack If you don't know how to use the Aob, look at the Hacking FAQ or the Guide to the Basics Also, now you can give back to this community and post your newly-found AoB on the forums! (Sorry, but the one for Creeper World Training Sim has already been posted! ? (broken image removed)) Finally, thanks to KH for hosting this awesome forum, and thanks to all you crazy hackers who have taught me everything I know about hacking!
|
|
Additional Info
|
So the code...it came out ugly
|
|
Level: 1
ADR Info
Additional Info
|
Yeah...? Not to for sure what to do with that.? We don't exactly have BBCodes...? We have HTML!
Anyway, when I get some time, I have to get karma set up and will get on fixing this post.? :)
|
|
Level: 1
ADR Info
Additional Info
|
Figured it out!? I was missing PRE tags from the accepted HTML list.? Fixed.? :)
|
|
Additional Info
|
Hey man please don't use the banhammer on me for saying this but ...
can you enable word wrap or format the first post nicely? It's not a biggie but can be quite tedious to scroll left and right to read everything you written. Thanks |
|
Level: 1
ADR Info
Additional Info
|
Those are all in PRE tags. There isn't a magic word wrap on PRE tags. You can't "enable" it either, since "word wrap" is always on in HTML.
|
|
Additional Info
|
On another note tim, the post looks nice but it fucked up your three banners for staff/donate/l33th4x. not sure if you care about that kinda thing or not, but figured id point it out
|
|
Additional Info
|
@TheIgnorantMasses. just a noob questions since im just starting flash hacking. I noticed that all the aobscan injection that i have found needs to be activated before the game is fully loaded. Is there a reason behind this? Can you modify actionscripts while the game is already loaded and runnning?
|
|
Additional Info
|
joemoney Posted on: 11/01/2013 8:29am @TheIgnorantMasses. just a noob questions since im just starting flash hacking. I noticed that all the aobscan injection that i have found needs to be activated before the game is fully loaded. Is there a reason behind this? Can you modify actionscripts while the game is already loaded and runnnig you only load the swf once. we recommend doing it while the game loads, but in reality you can modify it anytime before it calls the part that you modify. doing it as it loads is pretty much a guarantee that you change it before it calls it. a lot of the times you enter them at menu screens
|
|
Level: 1
ADR Info
Additional Info
|
Thanks for catching that one TNC
|
|
Additional Info
|
no problem, boss.
|
|
Additional Info
|
Thanks a bunch guys... This will speed up my testing process as i dont have to frequently refresh the browser
|
|
Additional Info
|
... sorry, it seems a bit offending that I want to answer this question which directed to our master ...
and sorry, please be tolerated my broken English. I want to provide the detail for thenewcomer's answer. (well , thenewcomer share the power of our master, so he is not offending in any sense, ha ;) ) If you noticed some codes post by EHoK, it required that it ativated AFTER some actions (eg, player got damaged for invincible). Such code also look a bit difference from other Flash aob. Because such aob is modifying native code of your machine (ie. x86 machine code).. Flash 9+ game has a much better performance than Flash 8- game, I think mainly because Flash 9+ game's bytecode source is converting to native code by a Compiler before execution , while Flash 8- is most likely interpreting. The Flash 9+ compiling is in some kind of 'Just in time compiling', I'm not pro, but I think that mean the compiler does not convert the bytecode source to native code all from the start, but a part by a part as need. That left a chance to modifyiing bytecode source. So if the aob is targeting the bytecode source, it has to be activate BEFORE the compiling, while EHoK's code is targeting native code, it has to be activated AFTER compiling. I think Unity Game that using IL-Code is similar to Flash 9+ game situation. bye~ No +karma or thanks post please, |
|
Additional Info
|
Off topic question:
For example there is a code for calculate damage something like: //health(100) 24 64 //damage(10) 24 0a //subtract a1 And this will subtract damage from health which results to 90. So the aob will be 24 64 24 0a a1 I saw one of haenawolf's aob hack that he changed a1(subtract) to 29(pop). 26 64 24 0a 29 I have read that 29 pops the value from the top stack. My question is, which value is being popped? the health or the damage? If health, what will happen to damage? Im just curious and would like to know/understand how it works. |
|
Additional Info
|
Hi,
Stack is last-in-first-out (by push/pop), so //My question is, which value is being popped? the health or the damage? damage is poped ... //If health, what will happen to damage? ... and gone. health is now at stack top, ready for next command's purpose, eg. an assignment to its original variable. Actually, an assignment (the 61 / 68 or D5/D6/D7 etc.) is also a 'pop', but get use the value of the stack top. bye~ No +karma or thanks post please, |